






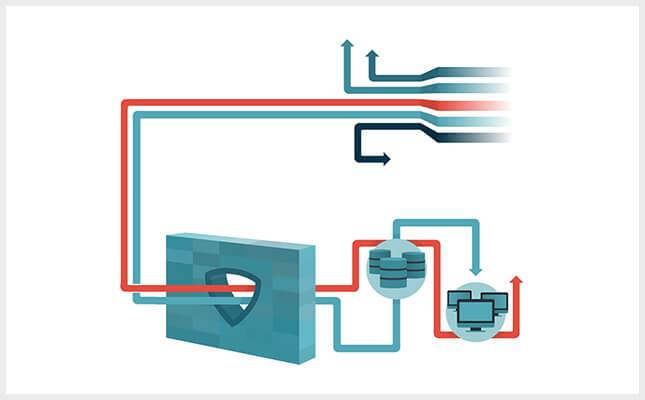
Penetration test is a simulation of an intruder's actions to penetrate the Customer's information system.
Thus, the penetration test allows you to identify vulnerabilities in the protection of your network and, if possible, to perform a demonstration hack.
XRAY CyberSecurity conducts security assessments in the following areas:


The objects of testing can be both the infrastructure as a whole or individual IT-systems and components:


















 PCI Data Security Standard (PCI DSS)
PCI Data Security Standard (PCI DSS)
 ISO/IEC 27001
ISO/IEC 27001

If you need to conduct penetration testing due to additional requirements, such as external regulators or the parent company, please contact us to discuss
Get a consultation



